Os2 bottles
'Tsunami' Trojan malware bot ported to OS X
Another day, another Trojan. The malware bot called "Tsunami" that has been developed for Linux systems since around 2002 has been found on OS X.
The malware (OSX/Tsunami.A) is a minimal threat, and like other Trojans and backdoors for OS X requires you to manually install it. While it is almost irrelevant to most users, it is out there and has the potential to cause harm for some.
The malware is an IRC bot, which is a program that connects to Internet Relay Chat (IRC) network servers and channels, where it can be controlled as a client for distributed denial-of-service (DDoS) attacks on targeted systems and networks. In addition it has the capability to both download files to an infected system and run shell commands (terminal commands) on it.
The current OS X variants of this malware appear not to work and may be in testing phases.
IRC bots are common programs used for numerous legitimate activities on IRC servers, but as with other well-intentioned routines, there is the potential for these bots to be developed and used for malicious activities.
Malware detection group ESET is claiming that so far there are two variants of this malware that connect to different IRC servers and channels. Both variants require someone to manually open the installer file, which then performs the following actions:
- It installs the malware in the /usr/sbin/ directory.
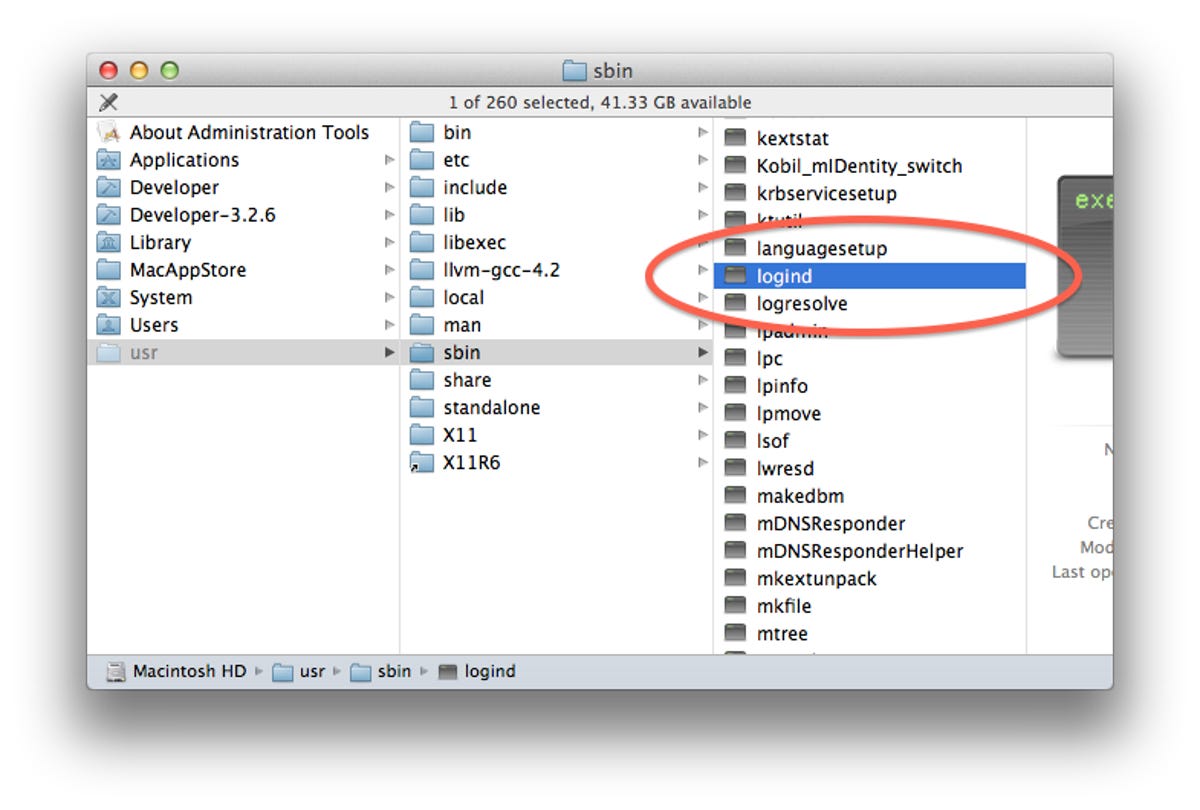
The malware is cleverly disguised as a command-line tool called "logind" that may appear to be important to the system. In OS X various background programs are called daemons and end with a "d" in their name to denote this. The malware both attempts to emulate this, and also places it in a hidden system directory (/usr/sbin) where other background services reside so it may blend in.OS X does have a background tool that is called "logind" but this resides in the /System/Library/CoreServices/ directory and not in the /usr/sbin/ directory.
- It modifies a system launch daemon.
The real OS X logind process (the one in the system's CoreServices directory) is managed by a system launch daemon called "com.apple.logind.plist" located in the /System/Library/LaunchDaemons/ directory, but when the Tsunami malware is installed, it replaces the contents of this launch daemon file with code that automatically launches the malware at startup and keeps it running on the system.
The correct version of this property list file should read as the following:

If the malware is installed on the system, the contents of this file will be replaced and you will instead see the following:

As with other Trojan horses, this malware is a minimal threat, and also should be caught if you have a tool installed like Little Snitch, which will detect when programs and background services try to contact servers on the Internet. If you have Little Snitch installed and see an attempt by a process try to contact the servers "pingu.anonops.li" or "x.lisp.su"--or, for that matter, or any other server, especially if it is using the port 6667 (a port commonly used for distributing malware via IRC connections)--then deny it access and check to see if the malware is installed.
To see if the malware is installed on your system, go to the /Macintosh HD/System/Library/LaunchDaemons/ directory and open the file called "com.apple.logind.plist." Compare it with the screenshots above, and if it looks like the second one, then replace its contents with what's shown in the first screenshot. Since this file is in a system directory, you may need a tool like TextWrangler to be able to authenticate properly and edit the file.
In addition to reverting the changed launch daemon file, check to see if the rogue logind process has been installed on your system. In the Finder, choose "Go to Folder" from the Go menu and then enter "/usr/sbin" in the text field. The Finder should open the hidden system directory, in which you can search for and remove the file called "logind" if it is present. When you remove it, the system will ask you for an administrator password, so provide it and then delete the file.
Beyond manually removing the malware, since the Mac version of Tsunami was found on October 25 various malware definitions, including those from F-Secure and Intego, have been updated to detect and remove this malware from systems, so be sure to keep your computer's antivirus definitions updated.
Questions? Comments? Have a fix? Post them below or e-mail us!
Be sure to check us out on Twitter and the CNET Mac forums.
Source
Blog Archive
-
▼
2023
(199)
-
▼
February
(44)
- Xiaomi Launches GoPro Rival With A Jaw-dropping Pr...
- You Can Now Listen To Podcasts On Twitter
- April Fools' Day Was A Huge Mistake And We Must Re...
- Westworld Season 3 Gets Futuristic Gadgets And Tec...
- Moto G7 Vs. G7 Play, G7 Power And G7 Plus: All Spe...
- Netflix Mulling $7 To $9 Monthly Price For Ad-Supp...
- Save $350 On One Of Our Favorite Chromebooks Of Th...
- Symantec Sale: Norton Security Slashed To $10 For ...
- How To Refinance Your Home
- Kia EV9 Electric Concept Previews A 3-row Producti...
- Moderna Sues Pfizer Over MRNA Technology Used In C...
- These Are The Cheapest Fruits And Veggies You Can ...
- 'The Rings Of Power': All The Tolkien Terminology ...
- 'Tsunami' Trojan Malware Bot Ported To OS X
- Coachbuilt Bentley Mulliner Batur Will Preview EV ...
- A Timeline Of The Biggest Ransomware Attacks
- Snapchat Wants To Put You In The Director's Seat W...
- Brew A Single Cup Or Whole Pot Easily With Hamilto...
- Amazon To Acquire One Medical In Major Boost To It...
- 12 Dynamic Gifts For 2-Year-Old Kids
- How Much Range You Really Need In An Electric Car
- AMD Radeon RX 6600 Tested: A Gaming GPU That Level...
- TikTok, YouTube, Snap Say Child Safety Is A Top Pr...
- Why Alcohol Actually Makes A Terrible Sleep Aid
- 10 Road Trip Essentials For Summer Travel
- Huawei Launches New Version Of P30 Pro Phone With ...
- How To Survive With An IPhone And A Windows Computer
- A Closer Look At The New MacBook Air M2
- Amazon Has $200 Off The Latest 16-inch MacBook Pro...
- Microsoft Says Windows 10X Isn't Happening
- HP's New Omen 15 Gaming Laptop Promises Big Perfor...
- DJI, FLIR Bring Stable Thermal Imaging To The Skie...
- How To Buy A Home In 2022: 6 Tips From A Real Esta...
- PC And Tablet Shipments Expected To Decline Throug...
- Beyond Axie Infinity: 'Web3 Games' Hope To Convert...
- Intel's Alder Lake Chip Could Speed PCs By 30% Whi...
- Need Better Cell Phone Reception? Try These 10 Tip...
- Moto G7 Vs. G7 Play, G7 Power And G7 Plus: All Spe...
- WWE Hell In A Cell 2019: How To Watch, Match Card,...
- 'Splatoon 3' Feels Familiar, But Fresh Features Hi...
- Xiaomi's Mi 10 Pro Looks Sleek And Modern With Its...
- Which MacBook Air M2 Charger Should I Get?
- Huawei's MatePad Pro Is A Good Tablet Trapped In A...
- Google ChromeOS Flex Is Now Ready To Run Your Old ...
-
▼
February
(44)
Total Pageviews
Search This Blog
Popular Posts
-
Contoh soalan fizik spm 2019, contoh soalan fizik spm 2018, contoh soalan fizik spm 2017, contoh soalan fizik kertas 3, contoh soalan fizik ...
-
Ukuran tv, ukuran tv 32 inch, ukuran tv 40 inch, ukuran tv 42 inch, ukuran tv 60 inch, ukuran tv 42, ukuran tv lcd, ukuran tv led, ukuran tv...
-
Ukuran sepatu, ukuran sepatu us, ukuran sepatu anak, ukuran sepatu eu, ukuran sepatu eur, ukuran sepatu nike, ukuran sepatu adidas, ukuran s...
